Over
a decade ago, I was put in charge of a group of projects. One of the
projects had been running for almost a year, but had never seen a single
live release to the customer! I realized there were too many unresolved
risks, and asked the concerned project manager to put risk management, a
new concept in the organization, as a top priority. Post identification
and qualification of risks, any risk above the risk threshold value had
to be brought down. If that was not done, I advised him no one should be allowed to work on the concerned project tasks.
This touched a raw-nerve.
One
day a senior executive dropped by and asked about the guidance I had
given to the project manager. In his mind, risk identification,
qualification, and addition of reserves et al are sufficient, and I
should not have stopped people from working on tasks.
My
response was: “When you know a cyclone is going to hit in five days, do
you wait to act on the fifth day or do you start immediately working to
mitigate the expected impact?”
To
elaborate a bit more, if a cyclone is about to hit, will risk
identification help? Will risk qualification help? You know it won’t do
much, though needed. How about quantification and adding reserves – say
various cyclone shelters, food stock, etc. – will those help? Yes, but
not fully. What is most needed in such a situation is risk mitigation.
We can’t change the probability of the cyclone, but the first act of
mitigation would be the evacuation of people. Risk mitigation is one
risk response strategy.
In this article, I’d like to explore various such strategies.
At
this stage, it’s important to note that risk response strategies are
applicable in cases of both negative risks (threats) and positive risks
(opportunities). You can learn more on individual project threats and
opportunities here.
Risk Response Planning
The
Project Management Body of Knowledge (PMBOK®) guide from the Project
Management Institute (PMI®) has a specific process to develop various
risk response strategies. It’s called Plan Risk Responses, and it’s
defined as follows:
Plan
Risk Responses is the process of developing options, selecting
strategies, and agreeing on actions to address overall project risk
exposure, as well as to treat individual project risks.
The
goal here is to develop risk response options, strategies, and actions
for both individual project risks and overall project risk. In other
words, you are planning to minimize the threats (negative risks) and
enhance opportunities (positive risks). With this process, the project
manager allocates resources and inserts items and activities within the
documents and the project management plan, in order to address said
risks.
Obviously, both the Risk Register and Risk Reports are
needed as inputs to address such risks (along with the Risk Management
Plan). Remember, we are addressing both individual risks and overall
project risk. See this depicted in the below flow diagram, with the highlighted process of Plan Risk Responses.
Risk Response Strategies – What Happens?
In the Plan Risk Responses process, for the negative risks, we are trying to move the High Probability and High Impact risks to be of Low Probability and Low Impact, by taking response actions. The reverse is also true.
I’ve explained this in the below video [duration: 3m: 53s], the content of which has been taken from RMP Live Lessons, Guaranteed Pass. For the best experience, you may want to go full-screen in HD mode and plug-in your earphones.
Risk Response Strategies for Threats
Now, let’s look at various response strategies for individual negative risks or threats.
Escalate Response Strategy
The escalate response strategy is used when the project team or the project sponsor agrees that:- The threat is outside the scope of the project.
- The project manager does not have the authority for the proposed response.
Example: A risk occurring in another project is impacting your project, so you escalate it to the level of a program or a portfolio.
Avoid Response Strategy
This response strategy is usually used for high priority risks, i.e., risks with high probability and a big negative impact. We can do two things here, either:
- Eliminate the risk completely, or,
- Protect the project from its impact.
Most of the time, the first (avoidance or elimination) is taken by changing the project management plan.
Example: You use a reliable technology platform for your project, instead of an unreliable, but cutting edge one.
Transfer Response Strategy *** UPDATED ***
Transfer
of a risk is done by shifting the impact to a 3rd party, who will own
the response. This method is usually best used for low impact risks. A
risk premium has to be paid to the 3rd party.
Example: You go for an incentivized contract, such as Cost Plus Incentive Fee (CPIF), to transfer the risks to the buyer.
For more information about incentivized contracts, go to these articles of point of total assumption and range of incentive effectiveness.
While the former is for Fixed Price Incentive Fee (FPIF) contract, the
latter is for CPIF contracts. Do note that by transferring the risks,
they are not gone! Rather, they will be addressed by the entity to which
risks have been transferred.
Mitigate Response Strategy *** UPDATED ***
With
a mitigate response strategy, you try to reduce the probability and/or
impact of the risk. This is used for high priority risks (with high P
and high I values). After reduction, the risk score should be within an
acceptable threshold limit. You can learn more about the usage of risk
threshold in this article on end-to-end risk management.
Example: You first build a prototype for a highly scalable product before going for full-fledged development.
Where mitigation is not possible due to probability, it’s best to look for mitigation responses which pull down the impact.
Accept Response Strategy *** UPDATED ***
In risk acceptance, no action is taken unless the risk occurs. Like transfer strategy, it’s used for low priority threats or used when it’s not possible to have a cost-effective solution which addresses the threat. The Project Management Plan is usually not changed in this case. A common risk acceptance strategy is to use contingency reserve.
Example: If there are frequent climate changes, you may accept such as a risk for your project.
Risk Response Strategies for Opportunities
Like threats, there also can be a number of risk response strategies for individual positive risks or opportunities.
Escalate Response Strategy
It’s
very similar to the one we have seen earlier for negative risks, except
that in this case it is for positive risks or opportunities. It’s used
when the project team or the project sponsor agrees that the threat is
outside the scope of the project and the project manager does not have
the authority for proposed response.
Again,
after escalation, the risk is not monitored by the team, but may be
recorded in the Risk Register. This is another key distinction for this
strategy compared to other strategies.
Example: A benefit occurring in another project has implications for your project and you escalate such to the level of a program.
Exploit Response Strategy
With
this risk response strategy, you seek to eliminate uncertainty by
ensuring that the opportunity is realized or that it definitely happens.
It’s used for high priority opportunities. A payment of a risk premium
can be involved for the party taking on the opportunity.
Example: Using talented resources to complete work early with less cost.
Share Response Strategy
In
this case, you allocate some or all of ownership of the opportunity to a
third party. Because it’s a share response strategy, both sides benefit
– the first owner and also the sharing owner. It can be considered the
“mirror” part of transfer response strategy, which we have seen earlier
for individual negative risks.
Unlike
transfer, it is not completely handed over to another party. It is
shared; however, risk sharing, like transfer response strategy, often
involves premium payment.
Example: Your
organization forms a joint venture or partnership with another
organization to execute the project considering the benefits involved
for both.
Enhance Response Strategy
With
this response strategy, you increase the probability and/or the impact
of an opportunity. Early enhancement is considered more effective. If
you cannot increase the probability, try to increase the impact.
Example: You add more features to a product to sell more products.
Accept Response Strategy *** UPDATED ***
In
this case, if the opportunity arises, it will be taken advantage of,
but not actively pursued. It’s usually considered for low priority
opportunities or if no cost-effective solution is available.
Example: A new project will takes advantage of a tax break, if an expected legislation is passed.
A Real-World Example and Exercise
Now that we have reviewed various risk response strategies, let’s do an exercise.
Scenario: You
are driving to reach your office and become aware of possible heavy
traffic on your traveling route through a radio warning or via global
positioning system (GPS). Regardless, you have to reach your destination
to attend an important meeting. You have the following options
available, outlined in the below table.
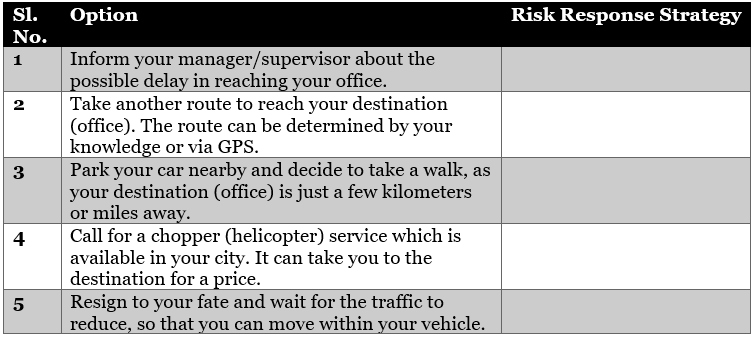
Can
you tell, based on the situation presented, which risk response
strategy will best fit? Do note that the scenarios presented are for
negative risks, and your response should be one of the strategies for
each question.
I would suggest that you try this exercise on
your own first before checking the solution, but I’ve explained in the
below video [duration: 7m: 20s], taken from my RMP Live Lessons course
what I advise. This clip also addresses an additional question related
to contingency reserve and how it’s used in our scenario.
Comparison
As
we reach the end of this article, I’d like to draw a comparison between
the risk response strategies for threats vs. opportunities in the below
table:

Finally,
it’s not that an individual threat will have a single response
strategy. If a threat can’t be avoided, then a project manager can
mitigate to a level where it becomes viable to accept or transfer it.
Similarly, if an opportunity can’t be fully exploited, it can be
enhanced to a level where it can be viable to accept or share it.
--
This article was first published by MPUG.com on 3rd May, 2022. This is an updated and refined version.
References:
[1] Course: RMP Live Lessons, Guaranteed Pass or Your Money Back, by Satya Narayan Dash
[2] Course: RMP 30 Contact Hours with Money Back Guarantee, by Satya Narayan Dash
[3] Book: I Want To Be A RMP, The Plain and Simple Way, Second Edition, by Satya Narayan Dash
.png)


thanks for sharing
ReplyDelete